Three weeks after Shimano was victim of a ransomware attack, hackers have made good on their threat of leaking the Japanese company’s data.
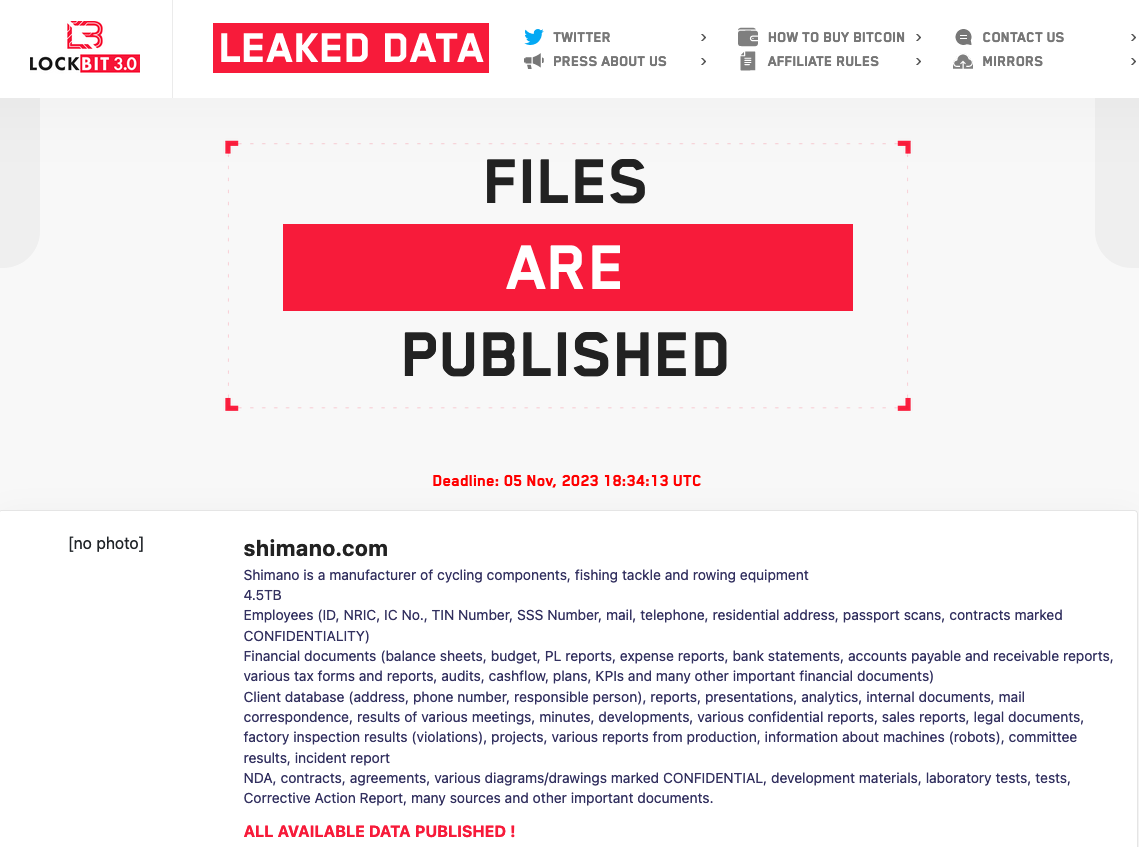
As first reported by Escape Collective, Shimano was ensnared by the LockBit group in early November, with the hackers at the time threatening to publish 4.5 TB of confidential data unless Shimano paid an unspecified ransom. This data, according to a notification published by the hackers on the LockBit website, included:
- Confidential employee details – including social security numbers, residential addresses, and passport scans
- Financial documents – including balance sheets, budget, bank statements, cashflow and tax details
- Client database – including contact details, reports, minutes from meetings, factory inspection results, incident reports, and legal documents
- Confidential diagrams and drawings, laboratory tests, NDAs, contracts, and development materials.
Three days later, when the November 5 deadline provided by the hackers was missed, the notice on LockBit’s website changed, stating that “all available data [had been] published”. For more than a fortnight, however, there was no corresponding download link to access the data. When contacted by Escape Collective, a cyber-security firm active in the space suggested that the delay in publication could indicate Shimano was in negotiations. Multiple attempts to contact LockBit itself via Sonar, a web messenger in the Tor darknet browser, went unanswered.
Finally, however, the other shoe has dropped. This week, the data – or at least a subset thereof – appears to have been published: multiple folders with subfolders upon subfolders nestled within them. Some documents are in English, some in Mandarin, some in Bahasa Indonesia, covering a broad range of information of varying confidentiality, across both Shimano’s fishing and cycling departments.
A lot of it is banal in the way that corporate documents often are, complete with dry PowerPoint presentations about HR processes. I doubt for instance, that Shimano is all that concerned about the sensitivities of the fact that they implemented a new ordering system at one of their factory canteens in November 2021. It’s also probably not a big deal if word gets out that they use a system of colour-coded baseball hats to denote seniority on the factory floor.
But there are greater sensitivities at play, including manufacturing data, sales projections, payroll spreadsheets with names of thousands of employees, vaccination statuses, and ‘medical surveillance’ information. Such data could be exploited by malicious actors, and underlines the risks businesses are exposed to in the event of a hack.
As for Shimano, the hack has been and gone, and the company self-evidently navigated the experience without paying a ransom to the criminals that gained access to their systems. But that doesn’t necessarily mean that the ordeal is over. At the bottom of the ransom note that Shimano would have received after being hacked, there’s an explicit threat: “If you do not pay the ransom, we will attack your company again in the future.”
Shimano was contacted for comment, with a spokesperson saying only that the incident “remains under investigation.”
Did we do a good job with this story?

